Powerful protection against threats. Accurate and easy to use.
“GravityZone Business Security” is a resource-saving cybersecurity package designed for all small and medium-sized businesses looking for the perfect balance between ease of use, performance, and cost. “GravityZone Business Security” is more than just business antivirus software:
1. It provides complete protection against all types of malware: ransomware, phishing, zero-day attacks, viruses, spyware, and more.
2. It utilizes machine learning methods, behavioral analysis, and continuous monitoring of running processes to keep up with the latest threats.
3. Everything is accessible on one, easy-to-use platform for all your devices: computers, mobile phones, physical and virtual servers.
The most effective end equipment protection
Combining EDR (Endpoint Detection and Response), risk analysis, and hardening technologies into one, single-agent console, "GravityZone" uses 30 advanced technological layers to successfully stop breaches throughout the threat lifecycle – from the first contact, exploitation, persistence, to malicious activity.
Endpoint detection and response technology
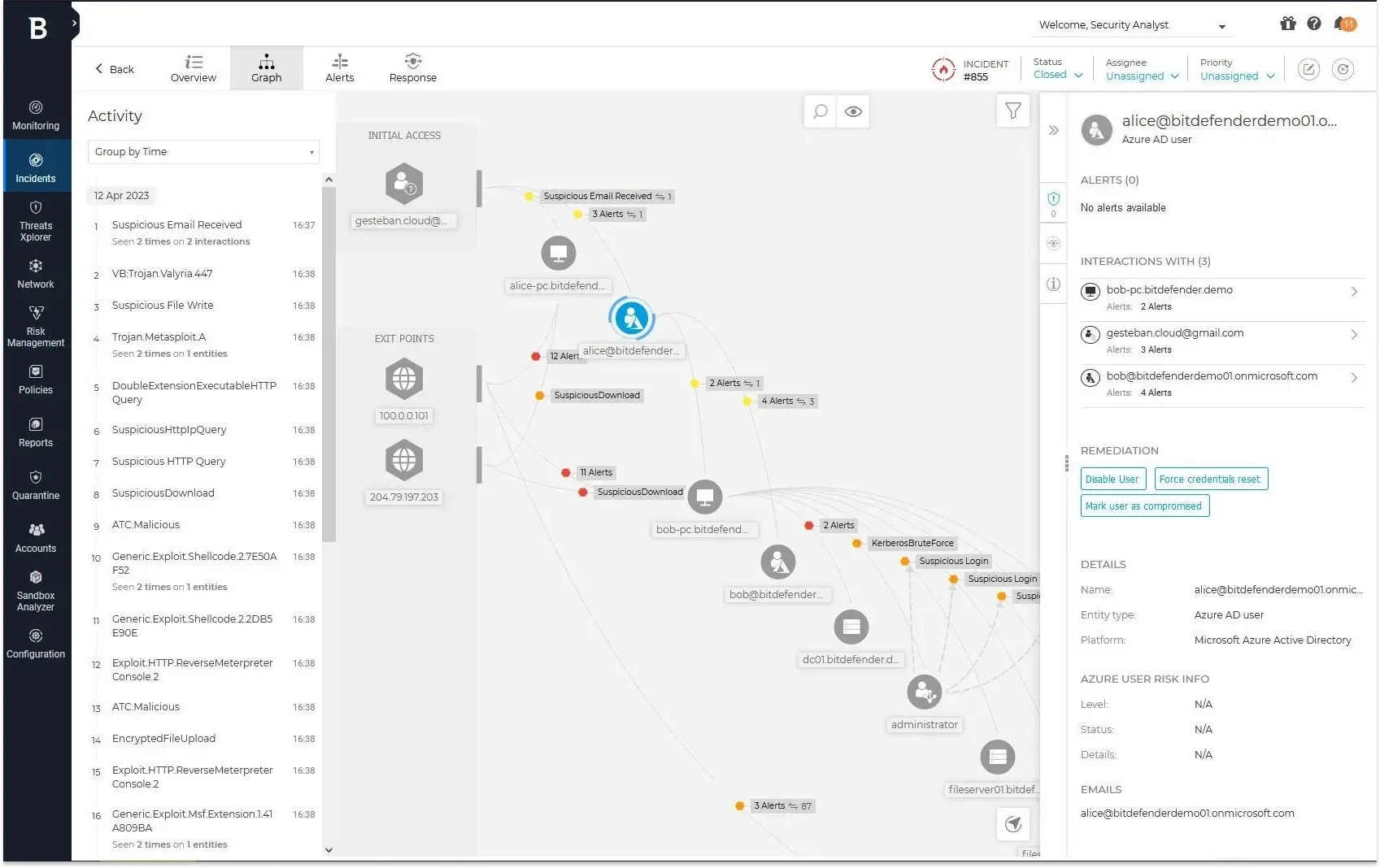
The new Bitdefender EDR expands EDR analysis and event correlation capabilities beyond a single endpoint, helping you combat complex cyberattacks involving multiple endpoints more effectively. Cross-endpoint detection and response uniquely provides threat visualizations at the organizational level, allowing you to focus on investigations and respond more efficiently and accurately.
Risk analysis-based hardening
The "Bitdefender" risk analysis engine continuously assesses endpoint security settings and user behavior, providing an easy-to-understand prioritized list of security improvements.
Main security levels
“Bitdefender” protects all your endpoints in physical, virtual, and cloud environments. This way, the software features ensure the security of your devices and prevent threats by detecting and protecting against them.
Combined antivirus / anti-malware program
Bitdefender" is a comprehensive cybersecurity suite that reduces the likelihood of breaches, simplifies deployment, and lowers costs. The software blocks new threats and reduces the number of false positives.
Continuous process monitoring
“Bitdefender Process Inspector” monitors running processes and assesses for malicious actions. You will have protection against attacks and malware 24/7.
Content management
Plan or configure this controller to block URLs by category using the "Block / Allow exception" Table.
Device management
Choose which devices and device types can be launched and which will be blocked or scanned automatically.
Bitdefender GravityZone Business Security prices
| BUSINESS SECURITY | BUSINESS SECURITY PREMIUM | BUSINESS SECURITY ENTERPRISE | |
|---|---|---|---|
|
Fixing software security vulnerabilities
|
|
|
|
|
Web protection
|
|
|
|
|
Protection against exploit programs
|
|
|
|
|
External device management
|
|
|
|
|
Firewall
|
|
|
|
|
Device risk analysis
|
|
|
|
|
Protection against network-based attacks
|
|
|
|
|
Automatic malware isolation and detailed analysis
|
-
|
|
|
|
Continuous monitoring of processes
|
-
|
|
|
|
Advanced threat intelligence
|
-
|
|
|
|
EDR (English: Endpoint detection and response)
|
-
|
|
|
|
XDR (English eXtended detection and response)
|
-
|
-
|
|
|
Price excluding VAT (with a 12-month commitment)
|
2.90
Eur/month.
|
3.90
Eur/month.
|
7.49
Eur/month.
|
|
Email Security
|
2.79 Eur / month
|
2.79 Eur / month
|
2.79 Eur / month
|
|
Mobile Device Security (eng. Security for Mobile)
|
3.29 Eur / month
|
3.29 Eur / month
|
3.29 Eur / month
|
|
Integrity Monitoring
|
2.99 Eur / month
|
2.99 Eur / month
|
2.99 Eur / month
|
Bitdefender Device Risk Analysis

Bitdefender Advanced Threat Security
Program management
Device management

Bitdefender protection against exploit programs
Bitdefender protection against execution attacks
Bitdefender Machine Learning
Bitdefender protection against network-based attacks
Bitdefender firewall
Bitdefender Automatic malware isolation
Bitdefender Automatic removal of executable files
Bitdefender anomaly detection
Bitdefender prioritized threat detection
Bitdefender Incident origin analysis
Bitdefender incident detection and analysis
Bitdefender
GravityZone

Anomaly detection
Bitdefender anomaly detection
Firewall
Bitdefender firewall
Automatic malware isolation
Bitdefender Automatic malware isolation
Automatic removal executed
Bitdefender Automatic removal of executable files
Analysis of the incident origin
Bitdefender Incident origin analysis
Protection against executive attacks
Bitdefender protection against execution attacks
Machine learning
Bitdefender Machine Learning
Protection against network-based attacks
Bitdefender protection against network-based attacks
Firewall
Bitdefender firewall
Automatic malware isolation
Bitdefender Automatic malware isolation
Automatic removal executed
Bitdefender Automatic removal of executable files
Anomaly detection
Bitdefender anomaly detection
Prioritized threat detection
Bitdefender prioritized threat detection
Analysis of the incident origin
Bitdefender Incident origin analysis
Incident detection and analysis
Bitdefender incident detection and analysis
Frequently Asked Questions (FAQ)
What is computer security?
(eng. Endpoint Security) is designed to protect devices (or endpoints) such as computers, mobile devices, or other endpoints from cyber threats. These protective measures aim to ensure that devices are safeguarded against malware, data theft, unauthorized network access, or other cyber attacks. Endpoint security often includes antivirus software, firewall software, behavior analysis, implementation of cybersecurity policies, and other technologies or procedures to ensure device protection and organizational data security.
What is Phishing?
Phishing is a cyber attack where intruders deceive individuals into providing sensitive information such as usernames, passwords, credit card details, or other personal information. This is usually done by impersonating a trusted entity, such as a bank, email service provider, or government agency, and sending fraudulent messages via email, SMS, or phone calls. These messages often contain links to misleading websites that mimic legitimate ones, tricking users into entering their confidential information. Phishing attacks are designed to exploit human psychology, often using urgency or fear tactics to prompt victims to act without verifying whether the request is genuine.
What is Ransomware?
Ransomware is malicious software that encrypts the victim's files or even the entire computer and demands a ransom for File restoration. This ransom is usually demanded to be paid in virtual currency to avoid data loss or public disclosure. Ransomware can enter the system through emails with malicious links, through dangerous websites, or through compromised software. The impact of these attacks can be very damaging to businesses or personal information, making it very important to regularly update security measures and educational activities to prevent ransomware attacks.
What is Malware?
Malware, a contraction of the words "malicious software," is a widely used term that encompasses various programs or code that have entered a computer or other device without Permission and perform harmful or illegal actions. Malware can be created with the intention of damaging data, stealing personal information, encrypting files through ransomware attacks, or other malicious activities. Malware can enter a device in various ways, such as emails with viruses, visiting dangerous websites, illegal programs, or compromised online sites. Preventive measures, such as antivirus programs and precautions while browsing online, are crucial to protect against malware attacks.
What is Endpoint Detection and Response, EDR?
(English: Endpoint Detection and Response, EDR) is a security technology designed to detect and respond to suspicious or malicious activities on endpoint devices such as computers, servers, or mobile devices. EDR systems continuously monitor devices, analyze their activity, and search for potential threats such as malware, signs of unauthorized activity, or vulnerabilities. When suspicious activities are detected, the EDR system can take automatic or manual response actions, such as isolating the incident, eliminating the threat, or sending alerts to security personnel. EDR is an important tool in organizations' security strategies, helping to ensure a rapid and effective response to cyber threats.
What is XDR?
Extended Detection and Response (XDR) is a security technology that integrates various data sources to detect and respond to cyber threats. Unlike traditional EDR systems, which typically operate only on endpoints, XDR encompasses a broader spectrum of data, including network, cloud, and other environmental elements.
XDR integrates various security tools and sources, such as endpoint, server, network logs, email servers, as well as non-traditional data sources like device monitoring systems. This allows the XDR system to create a wider picture of an organization's security posture and detect complex cyber threats that may go unnoticed using traditional security measures.
One of the main advantages of XDR is the ability to automate threat detection and response processes, improving incident detection and response times. Additionally, XDR can provide detailed event logs, data analysis, and security alerts that security professionals in the organization can use to more effectively protect the system from cyber threats.
What is MDR?
Managed Detection and Response (MDR) is a service provided by MDP CLOUD to detect and respond to cyber threats in an organization's system. MDR services often include external monitoring, threat detection, incident response, and investigations to reduce security vulnerabilities and impact on the organization.
MDR services include continuous network and system monitoring to detect suspicious or malicious activities. This may involve monitoring events and insights, analyzing security event logs, detecting threats using predefined patterns or sensors, as well as investigating and responding to breaches.
MDR services often also include proactive incident response, where detected threats are immediately investigated and neutralized to minimize damage to the organization. Additionally, MDR services may provide investigation reports that help the organization understand the incidents that occurred and gain insights into potential further threats.
The main advantage of MDR is that the organization's ability to detect and respond to cyber threats is in the hands of the service provider, allowing the organization to focus on its core activities and ensure that security is managed professionally and effectively.
What is zero-day vulnerability?
A Zero-Day Vulnerability is a cyber security flaw or weakness in software that has not yet been discovered or resolved by the manufacturer or development community. This type of vulnerability is called "zero-day" because when this flaw becomes known to the public, there is no time between the day of announcement and the exploitation of the vulnerability. This means that an attacker can exploit this flaw to gain access to a system or application before its owner has implemented any fixes or protective measures.
Zero-day vulnerabilities can be extremely dangerous because they allow attackers to target systems or applications with no prior warning or defense. Such flaws can be exploited in various ways, including the installation of malware, data theft, system disruption, or even persistent access to your system's control.
Organizations that are relatively vulnerable to zero-day vulnerabilities should be especially vigilant and implement proactive security measures, such as rapid response to threats, regular software updates, and vulnerability scanning. This will help reduce risk and protect the system from potential harm.
Get a personal Bitdefender GravityZone offer
Leave your contact information, and we will contact you within 1 business day.
Contact us 24/7
Blog
Effective queries for "Copilot

Microsoft 365 Copilot
how can the new AI assistant improve your work?

What is Microsoft Viva?
Microsoft Viva is an integrated workplace platform designed to enhance employee well-being, productivity, and collaboration in organizations.

End of Microsoft product support
Which "Microsoft" products are approaching the end of support?